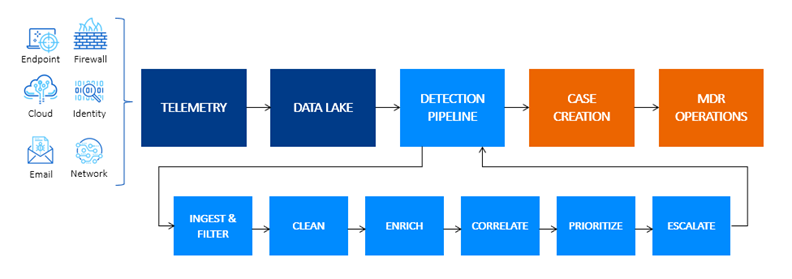
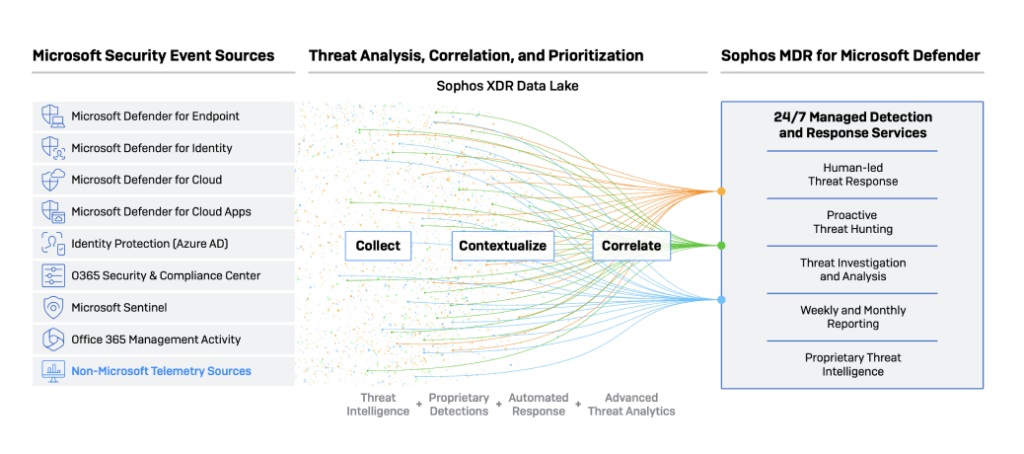
How AI Will Impact Cyber Attacks and Security
Within cyber security, the integration of Artificial Intelligence is a game-changer, enhancing the ability to detect and respond to threats swiftly and efficiently.
AI's role extends from automating complex processes to identifying patterns in data that may indicate potential security breaches.
The importance of cybersecurity for AI integration cannot be overstated; as AI systems become more integral to business operations, ensuring these systems are secure is paramount to prevent malicious exploits that could compromise sensitive information or disrupt services.
The Dual Nature of AI in Cyber Security
Artificial Intelligence in cyber security embodies a dual nature, serving both as a powerful ally and a potential adversary.
AI significantly bolsters cyber security defences, automating threat detection and response, and providing advanced analytics to predict and mitigate potential breaches. But at the same time, technological advancements empower cyber attackers, enabling them to devise sophisticated threats that can learn and adapt, making detection and prevention increasingly challenging.
This duality underscores the evolving landscape of cyber threats and defences.
Potential Cyber Threats Facilitated by AI
Artificial intelligence represents a shift, possessing a dual nature that both fortifies defences and elevates the sophistication of threats. AI's capability to automate attacks marks a significant evolution in cyber threats, enabling malicious actors to execute large-scale operations with unprecedented speed and efficiency. These automated systems, powered by AI, can swiftly adapt to countermeasures, making them formidable enemies against traditional security protocols.
AI Social Engineering

AI's prowess in mimicking human behavior and communication has revolutionised social engineering tactics.
By leveraging natural language processing and machine learning, AI can craft highly convincing phishing emails and messages that closely mimic legitimate communications, making it increasingly challenging for individuals to discern malicious intent.
This level of sophistication in phishing attacks not only enhances their success rate but also signifies a shift towards more personalised and targeted cyber threats.
Large Scale Data
AI-driven tools can analyse vast datasets to identify potential vulnerabilities and craft attack vectors that are highly tailored to their targets. This capacity for personalised threat creation makes AI an invaluable asset in the arsenal of cybercriminals, necessitating a corresponding leap in the sophistication of cybersecurity defences to mitigate these advanced threats effectively.
The AI Cyber Attacks That Could Impact Your Business
The integration of AI into cyber operations has significantly altered the risk landscape for businesses. This evolution presents both opportunities and challenges in safeguarding digital assets. Traditional cybersecurity approaches, which often rely on predefined rules and historical threat databases, are increasingly inadequate against AI-driven threats. These threats are characterised by their adaptability, speed, and the ability to learn from and circumvent conventional defence mechanisms.
The dynamic nature of AI-driven threats necessitates a reevaluation of cyber security strategies. Businesses must now contend with attacks that can rapidly evolve, using AI to analyse defences and devise new infiltration methods. This constant arms race between threat actors and defenders underscores the need for adaptive, intelligent security solutions that can anticipate and neutralise threats in real-time.
Case studies highlight the tangible impact of AI-driven cyber attacks on businesses. For instance, sophisticated phishing schemes using AI to mimic trusted contacts have led to significant financial losses and data breaches.
AI-powered ransomware attacks have become more targeted, leveraging machine learning to identify and encrypt the most critical business data, thereby increasing the pressure on organisations to pay ransoms.
To navigate this enhanced risk landscape, businesses must invest in advanced AI-driven security tools and adopt a proactive, rather than reactive, approach to cybersecurity. Emphasising continuous monitoring, threat intelligence, and predictive analytics can help in identifying potential vulnerabilities before they are exploited, thereby fortifying defences against the ever-evolving threat posed by malicious AI applications.
Defending Your Business Against AI Cyber Attacks
To effectively defend your business against AI-driven cyber threats, it's important to build a cyber security strategy that leverages AI-powered threat detection and response systems, integrate AI into your cyber security strategies, and enhance training and awareness programs.

AI-Powered Threat Detection and Response Systems: Implementing AI-driven solutions can significantly improve the ability to identify and mitigate threats in real time. These systems analyse vast amounts of data to detect anomalies that may indicate a security breach, enabling quicker and more accurate responses than traditional methods.
Incorporating AI into Cybersecurity Strategies: Integrating AI into cybersecurity frameworks involves not just deploying AI-based tools but also rethinking security protocols and infrastructure to support dynamic and intelligent defence mechanisms. This integration allows businesses to stay ahead of sophisticated cyber threats by continuously learning and adapting to new attack vectors.
Training and Awareness for Recognising AI-Driven Threats: Educating employees about the nature of AI-driven threats and the tactics used by attackers is crucial. Regular training sessions can help in developing a security-conscious culture, enabling staff to recognise and respond to potential threats effectively.
| Type of Cyber Threat/Attack | AI Advancement | Defence Mechanism |
|---|---|---|
| Phishing Attacks | AI can generate more convincing fake emails by learning from vast datasets. | Implement advanced email filtering that uses AI to detect sophisticated phishing attempts. Conduct phishing simulations & security awareness training to help your users spot phishing emails. |
| Ransomware | AI algorithms can identify the most critical data for encryption to demand higher ransoms. | Use AI-powered anti-malware tools that adapt to new ransomware signatures. |
| DDoS Attacks | AI can optimise attack strategies in real-time, targeting the most impactful areas. | Deploy AI-enhanced DDoS mitigation services that dynamically adjust defences. |
| Insider Threats | AI can mimic legitimate user behavior, making malicious activities harder to detect. | Employ AI-driven user behavior analytics to identify subtle anomalies indicative of insider threats. |
| Advanced Persistent Threats (APTs) | AI can automate complex attack strategies, continuously adapting to evade detection. | Leverage AI-based continuous monitoring and intrusion detection systems to counter adaptive APT tactics. |
How Will AI Cyber Threats Change?
The future of AI-driven cyber threats is poised for significant evolution, with these threats becoming more sophisticated and harder to detect.
As AI technologies advance, so too will the methods employed by cyber criminals, leveraging AI to automate attacks, personalise phishing attempts, and develop malware that can adapt to countermeasures.
Emerging technologies like quantum computing could further impact cybersecurity by potentially breaking traditional encryption methods, necessitating the development of quantum-resistant cryptography.
The integration of AI in cybersecurity strategies will be crucial, requiring continuous innovation and adaptation to stay ahead of threats.